IAM Policy
- Created using JSON
- A statement only applies if the interaction matches the Action and Resource
Statement Structure
Statement ID: optional, identify a statement, name of a statement
Action: specify the action, format: xx:xxx, e.g. [“s3: *”]
Resource: specify AWS resources
Effect: allow or deny
Diagram(in this case, user can perform any actions on S3, except on catgifs bucket):
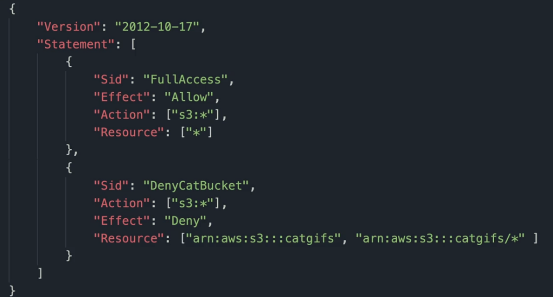
Overlap Situation
Explicit deny: overrule everything
Explicit allow: take effect unless there is also an explicit deny
Default deny: exists when there no explicit deny or explicit allow. Means when there is no explicit allow to a resource, people except root account user won’t have the access
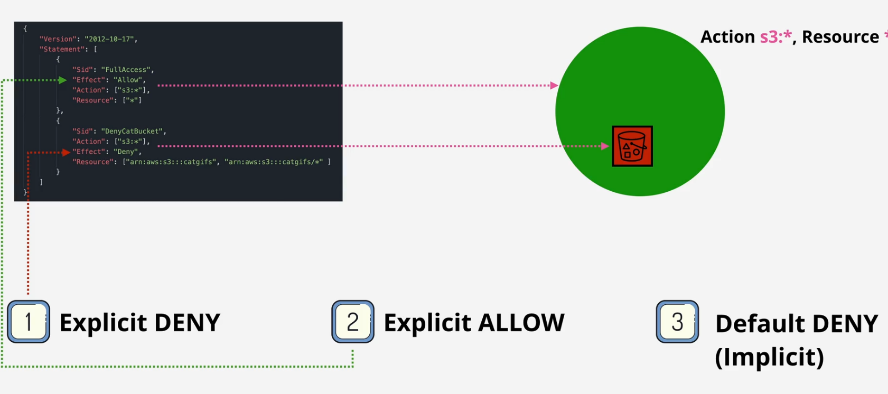
Policy Type
- Inline Policy: to individual identity, used to special or exception allow or deny
- Managed Policy: can attach to any identity, reusable, low management overhead, used for default management
- AWS managed polify
- Diagram:
IAM Users
5000 IAM users in a single accounts(ex)
IAM user can be a member of 10 groups at most (ex)
IAM users are identity used for any requiring long-term AWS access e.g. Humans, Applications or service accounts
If you can picture 1 specific thing, 99% percent choice is IAM user
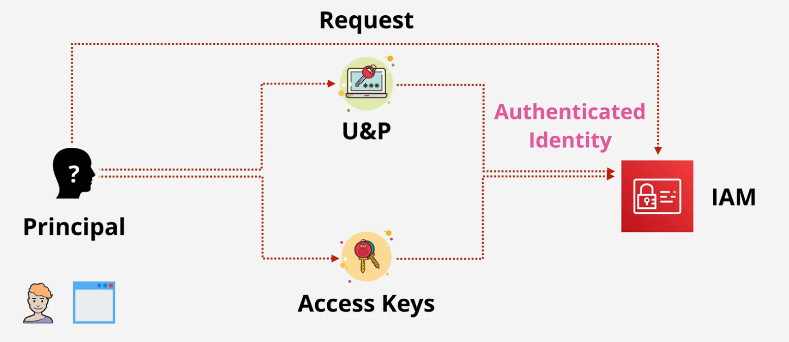
Authentication for IAM user is done by U&P and access keys
Authentication: a principal prove he or she is the IAM
Authorization: IAM checking statements apply for the identity denying or allowing the process
Authentication diagram:
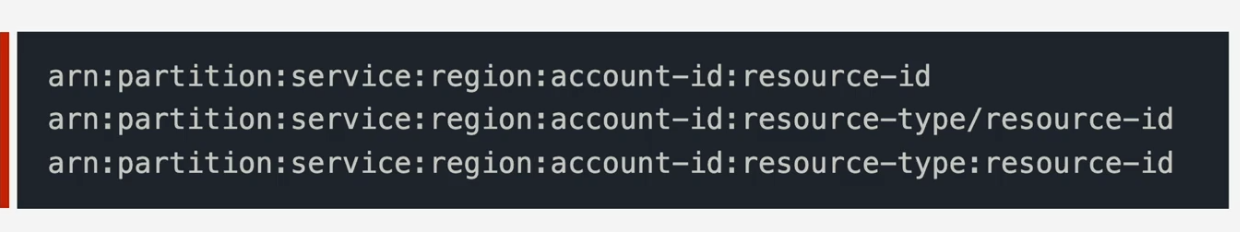
ARN(Amazon Resource Name)
Unique identity resources within any AWS accounts
arn:aws:s3:::catgifs - represents the bucket itself
arn:aws:s3:::catgifs/* - represents any objects inside the catgifs bucket
In the above ARN ::: means, s3 does not need region or account id
double colons: means nothing is between it, the field does not need to be specified
ARN diagram:
IMA Group
- IMA group are container for IMA users
- Can’t login IMA group, no credential on their own(ex)
- An IMA user could be in multiple IMA group(ex)
- Group could be attached with inline policy or managed policy
- For a IMA users in groups, there could be multiple policies attached to it. Apply d-a-d to these statements to decide deny or allow
- There is no built-in all user group, one should create and manage own their own
- **Can not **have groups inside groups
- A resource policy can not grant access to an IAM group, IAM group is not a true identity

